Understanding Your Cyber Risk Exposure
E=MC²
E (Cyber Risk Exposure) = M (Mitigation Effectiveness) x C (Cybersecurity Posture)²
Use our one-of-a-kind method to manage Cyber Risk to cut down weak spots and boost your company's security stance.
- Find weak points with Vulnerability Assessment Reports
- Beef up defenses with ISO 27001 Consulting
- Build a security-first mindset to maximize Mitigation Effectiveness.
Hacker Gazing
Vigilance in the Digital Cosmos
Think about the age-old practice of stargazing. For centuries, navigators, scientists, and even everyday people have looked to the stars to understand their place in the universe, to predict patterns, and to chart their course. It's about careful observation, analysis, and anticipating what might be coming.

Penetration Testing (VAPT Assessment) copies real-world threats.
Continuous Threat Detection Systems keep an eye on odd activity as it happens.
Useful Intel to guide your security spending.
Fortify Your Web3 Ecosystem
Proactive Security for Block-chain Assets
As Web3 adoption grows, securing decentralized ecosystems is essential. AHAD’s Web3 Security Audits ensure blockchain-powered applications and smart contracts remain invulnerable to exploitation.
Smart Contract Security Reviews with automated and manual audits.
API and Wallet Security Analysis to mitigate risks.
Compliance with Blockchain Security Protocols for maximum resilience.
Cyber Heist
Under Attack? Get Help toNavigate the Cyber Storm
The alarms are blaring, systems are down, and you suspect a cyber heist is underway. It's a moment of panic, confusion, and uncertainty. You're facing a digital storm, and the stakes are incredibly high.
Don't Face the Cyber Storm Alone
Emergency Response - Contact Us Now!
Privacy Navigator
Navigating Your Way Through Data Privacy Regulations
With data privacy regulations like GDPR, CCPA, and ADGM, navigating their complexities can be daunting. AHAD Privacy Navigator keeps your organization in compliance while gaining customer trust.
- Data Privacy Compliance & Gap Analysis
- Multi-jurisdictional Regulatory Compliance Expertise
- ADHICS & GDPR Compliance Advisory

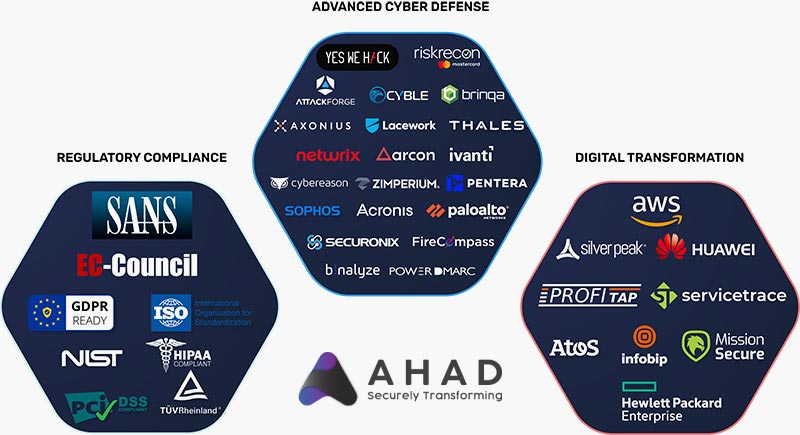
Why AHAD?
Navigating Your Way Through Data Privacy Regulations
- Regulatory Compliance Specialists: Large-scale experience with national and international frameworks, such as ISO 22301 Certification, ISO 42001 Implementation, and Personal Data Protection Law Compliance.
- Advanced Threat Detection Systems: Strong Credential Leak Monitoring and Account Hacking Prevention to protect your data.
- Security Posture Enhancement: We enhance your security culture and enhance your preparedness against cyber threats.